Difference between revisions of "How Apps Are Built"
(→Script) |
(→Script) |
||
| Line 16: | Line 16: | ||
:Every [[CNM app]] must communicate with [[WorldOpp Middleware]] using [[LDAP|Lightweight Directory Access Protocol]] ([[LDAP]]). If the ''COTS application'' lacks the ''LDAP'', ''API'', or other functionalities that [[CNM Cloud]] needs, an additional module or plugin is installed. | :Every [[CNM app]] must communicate with [[WorldOpp Middleware]] using [[LDAP|Lightweight Directory Access Protocol]] ([[LDAP]]). If the ''COTS application'' lacks the ''LDAP'', ''API'', or other functionalities that [[CNM Cloud]] needs, an additional module or plugin is installed. | ||
| − | :With regard to their ownership, all the ''COTS solutions'' such as core applications, modules, and plugins are divided in proprietary and [[open-source]]. ''Proprietary applications'' are owned privately; their code is closed. All [[CNM app]]s are [[open-source]]. That means that these ''applications'' are community-owned. Their code is open; any contributor may review and, if needed, modify it for | + | :With regard to their ownership, all the ''COTS solutions'' such as core applications, modules, and plugins are divided in proprietary and [[open-source]]. ''Proprietary applications'' are owned privately; their code is closed. All [[CNM app]]s are [[open-source]]. That means that these ''applications'' are community-owned. Their code is open; any contributor may review and, if needed, modify it for specific purposes. |
:Finally, ''COTS applications'' tend to be living projects; they are updated frequently, often, twice a year. [[CNM Cyber Team]] strives to update all [[CNM app]]s to last stable versions of the ''COTS applications'' that they use. The ''Team'' also makes best efforts to implement [[cyber-security]] patches and recommendations. | :Finally, ''COTS applications'' tend to be living projects; they are updated frequently, often, twice a year. [[CNM Cyber Team]] strives to update all [[CNM app]]s to last stable versions of the ''COTS applications'' that they use. The ''Team'' also makes best efforts to implement [[cyber-security]] patches and recommendations. | ||
Revision as of 17:24, 14 September 2020
How Apps Are Built (hereinafter, the Lectio) is the lesson part of the Soft behind CNM Cloud lesson that introduces its participants to CNM Cloud. This lesson belongs to the Introduction to CNM Cloud session of the CNM Cyber Orientation.
Contents
Content
The successor predecessor lectio is Engines and Organizers.
Key terms
Script
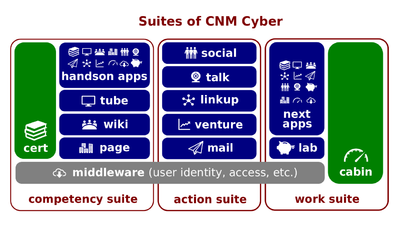
- Every CNM app consists of one or more end-user applications. Consequently, those applications consist of many software blocks such as customer data organizers, task work organizers, and wiki engines. Some applications are modular -- their blocks are separate modules plugged to the application's core.
- The overwhelming majority of the applications that CNM Cloud uses are commercial off-the-shell (COTS). Before being included in CNM Cloud, these applications were already available on the market to be installed and used.
- If any CNM app uses more than one end-user application, these applications are interconnected through application programming interfaces (APIs) to function as one CNM app.
- Every CNM app must communicate with WorldOpp Middleware using Lightweight Directory Access Protocol (LDAP). If the COTS application lacks the LDAP, API, or other functionalities that CNM Cloud needs, an additional module or plugin is installed.
- With regard to their ownership, all the COTS solutions such as core applications, modules, and plugins are divided in proprietary and open-source. Proprietary applications are owned privately; their code is closed. All CNM apps are open-source. That means that these applications are community-owned. Their code is open; any contributor may review and, if needed, modify it for specific purposes.
- Finally, COTS applications tend to be living projects; they are updated frequently, often, twice a year. CNM Cyber Team strives to update all CNM apps to last stable versions of the COTS applications that they use. The Team also makes best efforts to implement cyber-security patches and recommendations.
Available vs Custom Code is the successor lectio.
Questions
Lectio quiz
- The answer is recorded for the lectio completion purpose:
- CNM Cabin is hosted by:
- CNM Next Servers
- WorldOpp Federated Servers
- CNM Fellow Servers
- CNM HandsOn Servers
- None of the other answers is correct.
- Which statement below is correct:
- CNM Cyber may include three identical CNM apps.
- While taking this course, you work on the CNM Fellow Servers.
- Future administrators of CNM apps get hands-on training at the CNM Next Servers.
- All of the other substantive answers are correct.
- None of the other answers is correct.
- CNM Cabin is hosted by:
Placement entrance exam
True/False questions
- CNM Cloud Foundation has (does not have) four groups of servers.
- (wlcm-cloud-00003) Each of CNM Cyber's services is (not) powered by CNM app.
- (wlcm-cloud-00006) CNM Next Servers hosts systems used in hands-on training.
- (wlcm-cloud-00008) CNM HandsOn Servers is (not) designed to be used for training of CNM Cloud administrators and their experiments.
- CNM Cloud Foundation is (not) the combination of computing servers that host CNM Cloud.
- CNM Cloud Foundation is (not) the combination of computing servers.
- WorldOpp Federated Servers (do not) host WorldOpp Middleware and its software applications.
- Federated Server (does not) host CNM Cabin.
- WorldOpp Federated Server (does not) host CNM Cabin.
- CNM HandsOn Apps are (not) installed on the CNM HandsOn Servers.
- CNM HandsOn Servers are (not) used for the hands-on training of CNM Cyber service administrators.
- WikiHandsOn, TubeHandsOn, and MailHandsOn are (not) the examples of CNM HandsOn Apps.
- CNM Next Apps are (not) installed on CNM Next Servers.
- CNM Next Apps are (not) installed on WorldOpp Federated Servers.
- CNM Next Apps are (not) installed on CNM HandsOn Servers.
- CNM Next Servers are (not) used for the experiential learning of CNM Cloud administrators.
- CNM HandsOn Servers are (not) used for the experiential learning of CNM Cloud administrators.
Fill-in-blanks (short answer) questions
- CNM Cabin is hosted by _______ Server.
- CNM Next Apps are installed on CNM _______Servers.
- CNM _________Apps are installed on CNM Next Servers.
- CNM ____________ Servers are used for the experiential learning of CNM Cloud administrators.
- WikiHandsOn, TubeHandsOn, and MailHandsOn are the examples of CNM __________ Apps.
- For hands-on training during CNM Cyber Placement, you will be using CNM _________ Apps.
- CNM Cyber ___________ is the combination of computing servers that host CNM Cloud.
- Last, but not least, all the other CNM apps are installed on the CNM Fellow Servers.
- CNM Cert is installed on CNM _________ Server.
- CNM Page is installed on CNM _________ Server.
- CNM Wiki is installed on CNM _________ Server.
- CNM Tube is installed on CNM _________ Server.
- All the apps of the CNM Action Suite are installed on CNM __________ Server.