Difference between revisions of "Threat-response technique"
(Created page with "400px|thumb|right|[[Threat-response techniques]]A threat-response technique (hereinafter, the ''Technique'') is an established way for develop...") |
(→Related coursework) |
||
| Line 7: | Line 7: | ||
*[[Risk transference]]. Risk transference is seeking to shift the impact of a risk to a third party together with ownership of the response. | *[[Risk transference]]. Risk transference is seeking to shift the impact of a risk to a third party together with ownership of the response. | ||
| − | ==Related | + | ==Related lectures== |
*[[Enterprise Intelligence Quarter]]. | *[[Enterprise Intelligence Quarter]]. | ||
[[Category: Septem Artes Administrativi]][[Category: Articles]] | [[Category: Septem Artes Administrativi]][[Category: Articles]] | ||
Latest revision as of 19:49, 4 January 2019
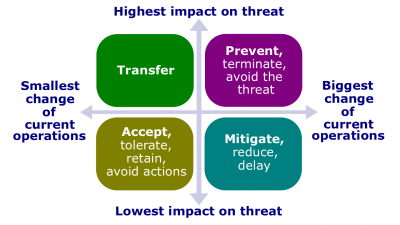
A threat-response technique (hereinafter, the Technique) is an established way for developing plans of responding to threats if they occur.
Types
- Risk acceptance (risk-response avoidance). This technique of the risk response planning process indicates that the project team has decided not to change the project plan to deal with a risk, or is unable to identify any other suitable response strategy.
- Threat prevention (threat avoidance). Risk avoidance is changing the project plan to eliminate the risk or to protect the project objectives from its impact. It is a tool of the risk response planning process.
- Threat mitigation. Risk mitigation seeks to reduce the probability and/or impact of a risk to below an acceptable threshold.
- Risk transference. Risk transference is seeking to shift the impact of a risk to a third party together with ownership of the response.