Difference between revisions of "Educaship Jitsi"
(→Software instances) |
(→Database system) |
||
| Line 7: | Line 7: | ||
: The [[product specification|''Product'' specifications]] are: | : The [[product specification|''Product'' specifications]] are: | ||
: CNM Jitsi has LDAP authentication and is hosted on a [[CNM ProxmoxVE|Proxmox cluster]] that ensures its high stability that distinguishes CNM Jitsi from [[Jitsi]]. | : CNM Jitsi has LDAP authentication and is hosted on a [[CNM ProxmoxVE|Proxmox cluster]] that ensures its high stability that distinguishes CNM Jitsi from [[Jitsi]]. | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
===Hosting=== | ===Hosting=== | ||
Revision as of 17:18, 12 April 2023
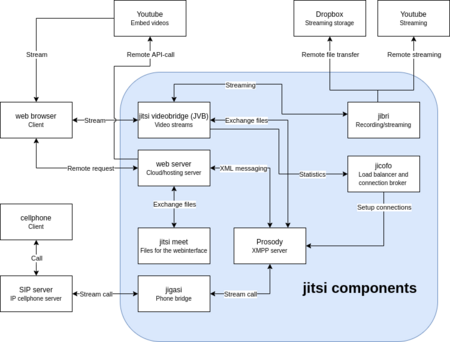
CNM Jitsi (hereinafter, the Soft) is a CNM stable app built with Jitsi. At this moment, it is unclear where and how this app will be finally installed since its HA and storage solutions haven't been designed yet.
Development of the Soft occurs under the Jitsi for CNM Cloud project.
Contents
Product specification
- The Product specifications are:
- CNM Jitsi has LDAP authentication and is hosted on a Proxmox cluster that ensures its high stability that distinguishes CNM Jitsi from Jitsi.
Hosting
- CNM Jitsi is installed on the CNM EndUser Farm on the Proxmox cluster, CNM Jitsi is a unique installation that is the first experience of the CNM EndUser Farm property - high availability. CNM Jitsi can migrate from one machine to another one that were added to Proxmox cluster. These machines are hosted by Hetzer. Read more about high availability: CNM EndUser Farm, CNM ProxmoxVE.
Software instances
- The software instance that powers core, hands-on training, and experiential systems.
Security
- For security, we use Fail2ban because it operates by monitoring log files (e.g. /var/log/auth.log, /var/log/apache/access.log, etc.) for selected entries and running scripts based on them. Most commonly this is used to block selected IP addresses that may belong to hosts that are trying to breach the system's security. It can ban any host IP address that makes too many login attempts or performs any other unwanted action within a time frame defined by the administrator. Includes support for both IPv4 and IPv6.
- Calls use the P2P mode, which is end-to-end encrypted via DTLS-SRTP between the two participants for encrypted communication (secure communication). Group calls also use DTLS-SRTP encryption, but rely on the Jitsi Videobridge (JVB) as video router, where packets are decrypted temporarily. All data is transmitted only through our server, and comprehensive TLS encryption provides protection against interception and unauthorized eavesdropping.
Malware protection
- Previously, CNM Cloud developers struggled with the viruses, so an effective anti-virus strategy must be found -- what was the solution?
Standing operating procedures
Monitoring process
- Monitoring is done in Nagios Snapshots are made by hand, not on CNM Jitsi. Read more: CNM Nagios.
Backup
- Usually the main backup is done on the farm, not on CNM Jitsi. So you can read more about backup on CNM EndUser Farm.
Snapshot
Versions and patch
System recovery
- How to install & Configure Jitsi: https://drive.google.com/file/d/14ynvD3wqliwynQr7TrBf6B-slxqmsDnn/view?usp=sharing
Customization
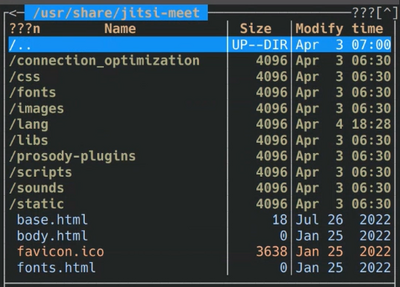
- To customize certain elements of Jitsi, you should:
- open the server where Jiti is installed in Terminal;
- open the Midnight Commander by using the command root@jitsi:/home/jitsi# mc;
- open catalog /usr (click /.. -> /.. -> /usr);
- open catalog /share -> /jitsi-meet
Hands-on assignments
- Hands-on assignments that CNM learners can use to get accustomed to the software while using its hands-on training systems and applications.
Presentations
- Presentations that present the software to its new users in multimedia, video, just audio, and/or just graphic formats.
User group
- CNM Social user group has not yet been created; the group may organize software-related events and produce newsletters.
See also
Related lectios
- Lectios that provide CNM learners with knowledge about the deployed software.