Privacy at CNMCyber
Privacy at CNM Cyber (hereinafter, the Lectio) is the lesson part of the Cyber Security Essentials lesson that introduces its participants to CNM Cabin. This lesson belongs to the Introduction to CNM Cyber session of the CNM Cyber Orientation.
Content
The predecessor lectio is User Data in Cyber.
Key terms
- User data. Any data that the end-user of a particular system creates or owns.
- Username (login name, account name, handle, or, rarely, ID). The humanly-readable name of user account that the end-user utilizes to access that account. A username is an essential part of user data.
- Password (passcode). Any string of characters that is used to confirm user's identity. The NIST Digital Identity Guidelines defines a password as "the secret is memorized by a party called the claimant while the party verifying the identity of the claimant is called the verifier. When the claimant successfully demonstrates knowledge of the password to the verifier through an established authentication protocol, the verifier is able to infer the claimant's identity.
Script
- The CNM Cyber Team strives to protect your sensitive data as much as the data can be protected.
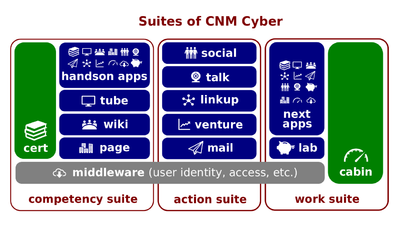
- For instance, the CNM Cyber Team cannot secure your posts at CNM Social, comments at CNM Page and CNM Tube, as well as anywhere where the other users can see openly them.
- Although the texts of your posts at CNM Cert and CNM Wiki cannot be private, the CNM Cyber Team may attempt to protect your identity, while assigning you a user alias and using that alias other than your username.
- Your sensitive data such as the one at CNM Cabin and CNM Mail is protected by cyber-security from unauthorized accesses and by privacy policy from improper use.
- The policy defines how the sensitive user data shall be secured. Particularly, every member of the CNM Cyber Team who has to access the data, must sign a non-disclosure agreement. The agreement legally-obligates the responsible Team member not to disclose any sensitive data related to a particular user.
sensitive user data from unwelcome use conducted by those users who are authorized to access that data.
ince data is stored remotely rather than your premise, apprehensions about data theft and privacy are obvious. But most cloud computing companies encrypt data while in transit or at rest. Also, their employees only get logical access to your data. Most companies adopt very strict protocols to ensure data security, confidentiality, and privacy.
If your data has peculiar security requirements, you could opt for a hybrid cloud where some data is stored with the cloud provider while some at your own premises.
- On the technology side, the administrators of CNM Cyber are required to follow general cyber-security rules -- all its software is regularly updated, new patches are timely applied, constant monitoring is in place, and so on.
- On the human side, each administrator who works on CNM Cyber generally and CNM Cabin especially is required to sign a non-disclosure agreement (NDA) that legally binds this administrator to keep your information secret.
What CNM Cloud Is is the successor lectio.
Questions
Lectio quiz
- The answer is recorded for the lectio completion purpose: