Difference between revisions of "CNM Lab Essentials"
(→Systems of CNM Lab) |
(→CNM Lab vs Wiki) |
||
| Line 3: | Line 3: | ||
The ''Lesson'' is preceded by the [[CNM Cert Essentials]] and succeeded by [[Action Suite Essentials]]. The ''Lesson'' is made up of five [[lectio]]s. At [[CNM Cyber]], the word, [[lectio]], is used for a lesson part. | The ''Lesson'' is preceded by the [[CNM Cert Essentials]] and succeeded by [[Action Suite Essentials]]. The ''Lesson'' is made up of five [[lectio]]s. At [[CNM Cyber]], the word, [[lectio]], is used for a lesson part. | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
==Cyber-Security at Lab== | ==Cyber-Security at Lab== | ||
Revision as of 22:31, 20 April 2020
CNM Lab Essentials (hereinafter, the Lesson) is the primary learning activity of CNM Cyber that introduces its participants to CNM Lab. The Lesson is the seventh of twelve activities that are designed to prepare its participants to the CNM Cyber Entrance Exam. All of those activities belong to the CNM Cyber Welcome Course (hereinafter, the Course).
The Lesson is preceded by the CNM Cert Essentials and succeeded by Action Suite Essentials. The Lesson is made up of five lectios. At CNM Cyber, the word, lectio, is used for a lesson part.
Contents
Cyber-Security at Lab
CNM Lab vs Wiki is the first lectio out of five ones that make up the Lesson.
Lectio 4 presentation
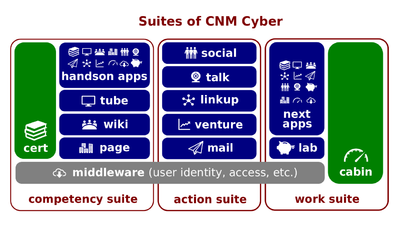
- Within CNM Cyber, CNM Lab stores the most security-sensitive technical accounts. CNM Lab contains every detail of CNM Cloud's architecture and all its private keys that can be used to access CNM Cloud's core.
- Cybercriminals can use those accounts in order to attack CNM Cyber. CNM Lab has to be highly cyber-secure in order to provide CNM Cyber with cyber-security.
- CNM Cabin stores user records and is equally secure. Both services make up the Work Suite.
Lectio 4 quiz questions
Review
- Which statement below is correct:
- A user of CNM Cyber should not necessarily be in a good standing in order to utilize services of CNM Lab.
- Every source code file must be uploaded to CNM Lab in order to be deployed within CNM Cyber.
- Authorized users of CNM Lab can identify which image file was last edited.
- All of the other substantive answers are correct.
- None of the other answers is correct.
- -- (wlcm--prvw)
Summaries
Predecessor
- The predecessor lesson is CNM Cert Essentials.
Outline
Successor
- No successor session is available in this Course, but the Course graduates are welcome to enroll in the CNM Cyber Orientation to become certified users of CNM Cyber.